Novel Approaches to securing ICOS continuum
As security attacks have become increasingly frequent and sophisticated, complex systems like ICOS for managing CloudEdgeIoT continuum, can be particularly vulnerable. To safeguard ICOS against security vulnerabilities and threats, we will also be using State-of-the-art approaches relying on AI (Artificial Intelligence).
AI can be used to rapidly identify and respond to security threats, analyse large amounts of data to detect patterns and anomalies, and provide insights into potential vulnerabilities. AI-powered security systems can also learn from previous attacks, making them more effective at protecting against future attacks. Despite the great potential of AI for improving cybersecurity, it has its limitations and vulnerabilities. This is why it is important that organizations use AI in conjunction with other existing security measures, such as firewalls, antivirus software, user training, and insider threat mitigation strategies to create a comprehensive holistic security strategy that addresses all potential threats.
An existing tried approach, which will be implemented in ICOS through the Security Scan module, is the “static” rule-based security monitoring. Tools like the Wazuh 1 use this static approach to make sure that the system is undergoing continuous runtime verification for any security concerns or violations. Such violations can be recognized by monitoring various security metrics (e.g., file integrity, network configuration changes, usage of software reported as vulnerable, malware detection) and integration with the monitoring component to recognize violations of defined security policies and alert DevSecOps teams to address and eliminate threats as fast as possible. If any erroneous or anomalous log entries appear, the Wazuh-based technology can alert the user according to the configured rules.
A novel, AI-based approach which complements static monitoring, is the “dynamic” anomaly detection utilizing machine learning. This is done through a novel LOg MOnitoring System (LOMOS), used in ICOS by the Anomaly detection module. LOMOS uses log data collected by different tools, e.g. Wazuh, to recheck metrics and events and assign them an anomaly score, promptly identifying anomalies while minimizing human intervention. Raw logs are processed by a Log Parser component. A sequence of log templates is the input into Masked Language Modeling (MLM), a common self-supervised Natural Language Processing (NLP) methodology to predict masked log templates in the sequence. Moreover, LOMOS uses Hypersphere Volume Minimization (HVM) assuming that ’normal’ samples can be mapped to close representations.
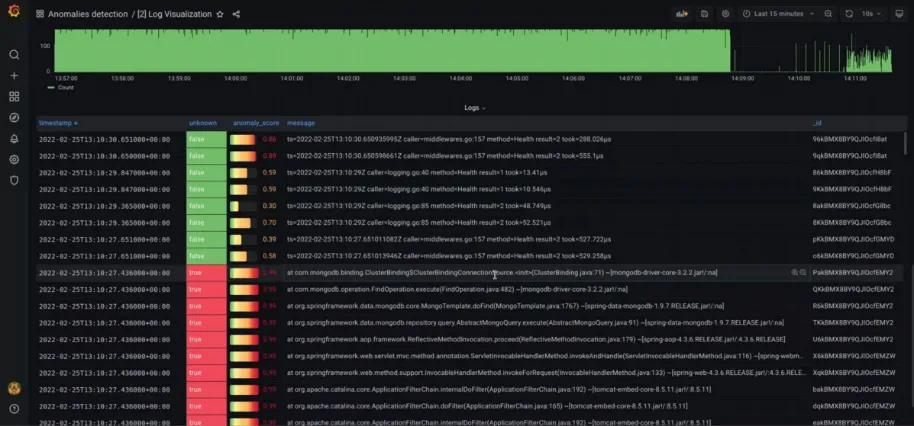
Figure 1: A screenshot of the dashboard for the self-supervised anomaly detection from logs showcasing threat levels and characteristics
Traditional log monitoring solutions are limited to rule based (manual) analysis of time series data. In contrast, LOMOS makes use of state-of-the-art Natural Language Processing architectures to model log streams and capture their normal operating conditions. This enables the implementation of a monitoring system that does not depend on any manually defined rules or human intervention but relies on that behavioural model to automatically detect deviations that would represent any kind of abnormal situation, including potential security threats. Our approach automatically analyses system or application logs and provides valuable insights regarding the current and past status of the monitored assets. The technology uses deep learning techniques, to compute anomaly score on sequences of log templates, applying NLP models to the IDs defined for the templates.
Both approaches work best in combination with each other to check deployed ICOS resources, detect security issues and quickly inform the user to take necessary measures or, through the Security Vulnerability Mitigation module, automatically execute certain mitigation or recovery actions.
For more information about the static and dynamic approach see here: Antić, J., Costa, J. P., Černivec, A., Cankar, M., Martinčič, T., Potočnik, A., ... & Boigues, I. T. (2023, April). Runtime security monitoring by an interplay between rule matching and deep learning-based anomaly detection on logs.
Footnotes


This project has received funding from the European Union’s HORIZON research and innovation programme under grant agreement No 101070177.


